Articles: search
3 item(s) found.
StegoWeb: Towards the Ideal Private Web Content Publishing Tool
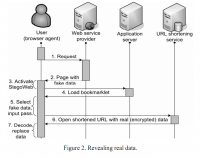 Privacy breaches through profiling constitute a considerable threat to users of Web 2.0 services. While many concepts have been proposed to address this issue by allowing users to encrypt, obfuscate, or otherwise conceal information of their choice, all have certain limitations. In this paper, we survey the available solutions, and propose a taxonomy for classifying them based on a revised evaluation scheme that builds upon our previous work. Our main contribution is a model that harnesses steganographic techniques in order to hide sensitive data, and the description of a proof-of-concept implementation thereof that allows a user to hide profile data on a website without installing any sort of software aside from a conventional web browser.
Privacy breaches through profiling constitute a considerable threat to users of Web 2.0 services. While many concepts have been proposed to address this issue by allowing users to encrypt, obfuscate, or otherwise conceal information of their choice, all have certain limitations. In this paper, we survey the available solutions, and propose a taxonomy for classifying them based on a revised evaluation scheme that builds upon our previous work. Our main contribution is a model that harnesses steganographic techniques in order to hide sensitive data, and the description of a proof-of-concept implementation thereof that allows a user to hide profile data on a website without installing any sort of software aside from a conventional web browser.
BlogCrypt: Private Content Publishing on the Web (2010)
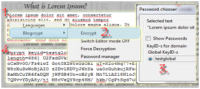 Voluntary disclosure of personal information is becoming more and more widespread with the advent of Web 2.0 services. Publishing such information constitutes new kinds of threats, such as further reinforcing already existing profiling techniques through correlation of perceived user activities to those publicly disclosed, but the most obvious of all is the intrinsic threat that malicious third parties collect and combine information we publish about ourselves. In this paper, we evaluate currently existing solutions that are destined for ad-dressing this issue, then propose a model of our own for pro-viding access control for a user over information she published and analyse our implementation thereof.
Voluntary disclosure of personal information is becoming more and more widespread with the advent of Web 2.0 services. Publishing such information constitutes new kinds of threats, such as further reinforcing already existing profiling techniques through correlation of perceived user activities to those publicly disclosed, but the most obvious of all is the intrinsic threat that malicious third parties collect and combine information we publish about ourselves. In this paper, we evaluate currently existing solutions that are destined for ad-dressing this issue, then propose a model of our own for pro-viding access control for a user over information she published and analyse our implementation thereof.
Comprehensive analysis of web privacy and anonymous web browsers: are next generation services based on collaborative filtering? (2008)
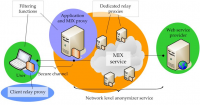 In general, networking privacy enhancing technologies are better on larger user bases - such criteria that can be enhanced by combining them with community based services. In this paper we present main web privacy issues and today’s complex preventive solutions, anonymous web browsers, in several aspects including a comprehensive taxonomy as a result of our inquiry. Also, we suggest a next generation anonymous browser scheme based on collaborative filtering concerning issues on semantic web. Finally we analyze the benefits and drawbacks of such services, also examining the possible investors and raised moral considerations.
In general, networking privacy enhancing technologies are better on larger user bases - such criteria that can be enhanced by combining them with community based services. In this paper we present main web privacy issues and today’s complex preventive solutions, anonymous web browsers, in several aspects including a comprehensive taxonomy as a result of our inquiry. Also, we suggest a next generation anonymous browser scheme based on collaborative filtering concerning issues on semantic web. Finally we analyze the benefits and drawbacks of such services, also examining the possible investors and raised moral considerations.
Source: In Proceedings of the Joint SPACE and TIME Workshops 2008 (pp. 17-32). Trondheim, Norway: CEUR-WS.
